Google Report Reveals How Text Scams Steal Your Data And Money
A Google report on Thursday said that iPhone users are more likely to receive scam texts and calls than Android users, thanks to Google's more advanced protections built into the operating system, including defenses powered by AI to detect and prevent potentially malicious behavior. Google provided data from three separate sources, including a survey it conducted and two reports from third parties. But Google released one other report, one that every phone user should read no matter what mobile platform they prefer. Google explained the anatomy of phone scams involving text messages from strangers, including the tactics they use ("Spray and Pray," and "Bait and Wait" attacks), the infrastructure, and the mind games they play with victims whom they hope to convince them to provide personal data or money.
Google notes that scammers stole $400 billion from consumers worldwide in the past year. Only about 4% of victims got their money back. Google found that employment fraud is the most common scam, promising income opportunities to steal personal and financial data. Financial scams are also widespread, including attacks that involve fake unpaid bills, subscriptions, fees, and investment schemes in cryptocurrency and other assets. The report also notes that scammers often try to impersonate package delivery firms and government agencies.
What are Spray and Pray and Bait and Wait?
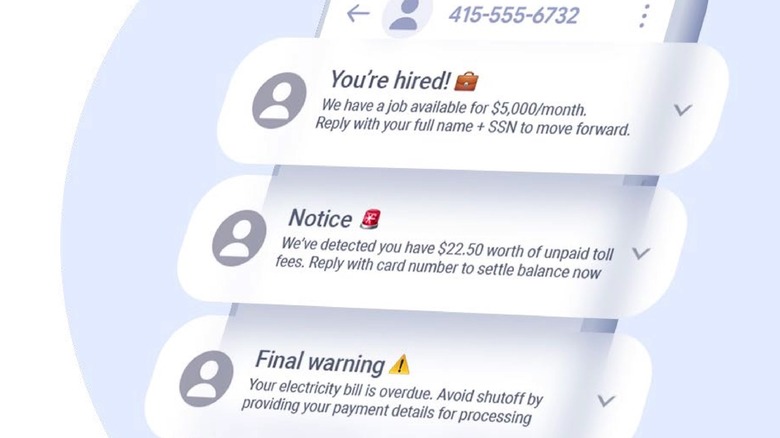
Google presented two distinct paths of deception that work on victims. Spray and Pray (image above) refers to high-volume attacks targeting millions of numbers. The attackers hope a small percentage of targets will respond. The messages are designed to feel urgent so user action seems necessary. They might refer to current events, like tax season, or fake delivery notifications. Once a victim texts back, the attacker tries to provoke an emotional response, with Google citing panic over a locked account or excitement for an investment opportunity. The user feels the pressure to act, and they might provide information or money to the attackers. The user might click a short link to a phishing page that can steal credentials, credit card details, and other data.
The Bait and Wait method (image below) has the same goal (steal user data or money), but uses a different approach. Google explains that this is "a slow, calculated, human-operated approach that relies on building a false relationship with a single person over time." The attack doesn't start with malicious links, but with a simple "Hello," or "Do you remember me?" message. The scammer poses as a friend or recruiter, slowly building up trust. Google notes that scammers end up instructing the victim to communicate over a third-party app to evade security and monitoring.
Recognizing these patterns in messages from unknown senders, verifying the claims they make, and avoiding an emotional response (the urgency to act) could help you secure your data and money.
Text scamming is a sophisticated business
The report notes that malicious individuals rely on both direct messages (DMs) and group messages (GMs) to find their victims. DMs were 20 times more common in the past year, but GMs now dominate the landscape. Attackers may have shifted to groups as these messages seem less suspicious than DMs from unknown numbers. Also, the group can widen the net for attackers, who pose as legitimate members.
Google's report also noted that attackers are more likely to send their spam messages at specific times. In the U.S., the attacks can start as early as 5 a.m. PT, peaking between 8 a.m. and 10 a.m., when many people start their day. Also, scammers tend to focus on the start of the week with their campaigns, with a high volume of texts registered on Monday, when unsuspecting victims are the busiest and least skeptical of unknown numbers.
A scamming "business" also involves complex logistics, as detailed in Google's report. Scammers have specific needs, like access to large lists of phone numbers they can target, which they often purchase from the Dark Web or by scraping legitimate websites. The attackers also operate or hire phone farms, which can include thousands of prepaid SIMs from around the world and special gear to make spam texting and calling as efficient as possible. Some bulk messaging services can deliver over a million messages per day at low cost. The attackers require "phishing-as-a-service" software for creating and hosting fake websites that look like legitimate banks, postal services, and other institutions.
Finally, the source of attacks moves around the world, as scammers choose SIMs from countries where it's easy to procure cards in bulk without encountering obstacles.